Real-Time Anomaly Detection with Kafka and AI Agents
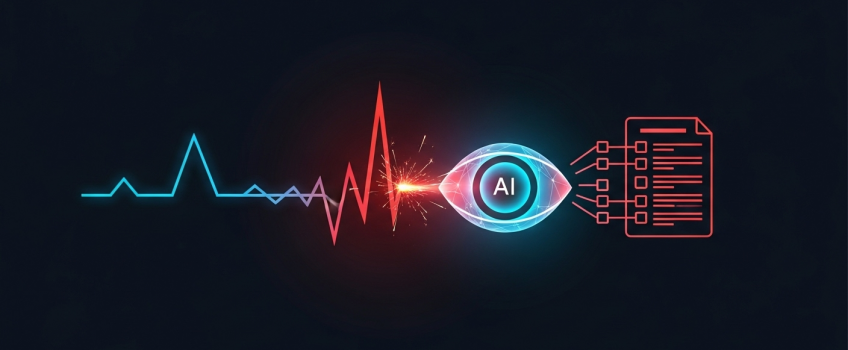
Real-Time Anomaly Detection: How an AI Agent Can Monitor a Kafka Topic and Create Automated Incident Reports
A critical alert fires: "P99 Latency > 500ms". An on-call engineer wakes up, opens a dashboard, and begins the frantic search for a cause. They sift through logs, check recent deployments, and try to correlate metrics, all while the clock is ticking. This manual, reactive process is the reality for most operations teams.
The critical "why": The problem isn't the alert; it's the lack of immediate context. What if the alert wasn't just a number, but came with a pre-packaged investigation report? What if an autonomous agent could perform the initial triage, gathering relevant data and synthesizing a summary before a human even opens their laptop? This is not just about faster response times; it's about transforming operations from reactive firefighting to proactive, intelligent problem-solving. At ActiveWizards, we build these systems by combining real-time data platforms with autonomous AI agents. This article provides a practical architectural guide.
Architecture: From Raw Stream to Intelligent Triage
A successful system requires a clear separation of concerns. We don't build one giant application. Instead, we create a multi-stage pipeline where each component has a specific job: one component detects the anomaly, another investigates, and a final one reports.
Diagram 1: The end-to-end architecture for an autonomous incident response agent.
Stage 1: Detecting Anomalies in Real-Time
The first step is to mathematically identify an anomaly. This is a classic stream processing task. A component, often built with Kafka Streams or Apache Flink, consumes the raw metrics stream. It maintains a stateful understanding of what's "normal" (e.g., a moving average and standard deviation for the last hour). When a new metric arrives that falls outside a defined threshold (e.g., more than 3 standard deviations from the mean), it publishes a structured "anomaly event" to a new Kafka topic. This event is the trigger for our AI agent.
Stage 2: The AI Investigator Agent
Upon receiving an anomaly event, the agent's job is to act like a skilled on-call engineer. It doesn't just pass the alert along; it performs an initial investigation by using a predefined set of tools.
The Agent's Toolkit
A production-grade agent needs tools to gather context from the same sources a human would:
- Metrics Query Tool: Connects to a system like Prometheus to ask follow-up questions. "OK, P99 latency is high. What is the P50 latency? And what is the error rate for the same time window?"
- Log Search Tool: Connects to a logging system like Elasticsearch or Loki to find correlated errors. "Show me all logs with level 'ERROR' or 'FATAL' from the affected service in the 5 minutes leading up to the anomaly."
- Deployment Log Tool: Connects to a CI/CD system or Git repository. "Was there a new deployment to production in the last hour? If so, what changed?"
# Conceptual setup for the Incident Response Agent
from langchain.agents import AgentExecutor, create_openai_functions_agent
from langchain_openai import ChatOpenAI
from langchain.tools import tool
# Assume tools like 'query_prometheus', 'search_es_logs', 'get_recent_deployments'
# are defined and decorated with @tool
tools = [query_prometheus, search_es_logs, get_recent_deployments]
llm = ChatOpenAI(model="gpt-4o")
# Prompt engineering is key here to guide the investigation process
prompt = ...
agent = create_openai_functions_agent(llm, tools, prompt)
agent_executor = AgentExecutor(agent=agent, tools=tools, verbose=True)
def handle_anomaly(anomaly_event: dict):
# The agent is given a structured task based on the anomaly event
task = f"""
Investigate a critical performance anomaly detected at {anomaly_event['timestamp']}.
The metric '{anomaly_event['metric_name']}' reported a value of {anomaly_event['value']},
which is outside the normal range.
Your mission is to:
1. Use your tools to gather context about related metrics, logs, and recent deployments.
2. Synthesize your findings into a structured incident report.
3. The report must include a summary, a list of observations, and a probable cause.
"""
report = agent_executor.invoke({"input": task})
# Send the report to Slack, Jira, etc.
# post_to_slack(report['output'])
Stage 3: Synthesizing the Incident Report
This is where the LLM's true power shines. After the agent has used its tools to collect raw data (metrics, logs, deployment info), it synthesizes this information into a human-readable report. This step transforms a flood of raw data into actionable insight.
The quality of the final report is entirely dependent on the quality of the synthesis prompt. A lazy prompt will produce a rambling paragraph. A well-engineered prompt will produce a structured, invaluable document. Your prompt should explicitly ask for a specific format:
**INCIDENT REPORT**
**Timestamp:** [Timestamp from event]
**Summary:** A one-sentence summary of the problem.
**Key Observations:** A bulleted list of facts gathered from the tools (e.g., "P99 latency spiked to 800ms", "Error logs show 'Connection Timeout' errors", "Deployment #5678 went live 10 minutes prior").
**Probable Cause:** The agent's best guess at the root cause based on the observations.
**Next Steps:** Recommended immediate actions for a human engineer.
This structure makes the output immediately useful and scannable.
Production-Ready Considerations
Before deploying an agent that can trigger alerts, consider these engineering realities:
- Alert Throttling & De-duplication: What happens during an "alert storm"? You need a mechanism (e.g., using a Redis lock) to prevent the agent from creating 1,000 incident reports for the same underlying issue.
- Tool Security: The agent's tools must use read-only credentials. You cannot risk an agent having the ability to change configurations or delete data.
- Cost Management: Each investigation is a series of LLM calls. Implement a budget and monitoring on your LLM API usage.
- Observability: How do you monitor the monitor? Use a tool like LangSmith to trace the agent's reasoning process, especially when it produces a confusing or incorrect report.
The ActiveWizards Advantage: Engineering Autonomous Operations
Building an autonomous monitoring agent is a powerful fusion of real-time data engineering and advanced AI. It requires a solid foundation in streaming data with Kafka, a deep understanding of agentic architecture, and a production-first mindset focused on reliability, security, and observability.
At ActiveWizards, we specialize in building these end-to-end systems. We don't just create AI models; we engineer the robust, data-aware autonomous systems that can be trusted to monitor and help manage your most critical business processes.
Transform Your Operations with Intelligent Automation
Tired of reactive firefighting? Our experts can help you design and build a custom autonomous monitoring agent that provides immediate context and accelerates your incident response.


Comments (0)
Add a new comment: